

How Tetragon Redefines Security and Observability

Kubernetes continues to be the favorite orchestration tool for most companies. This consistent demand means that the need for advanced security and observability solutions has never been greater. Tetragon, powered by the innovative eBPF technology, provides a groundbreaking approach to runtime security and system observability. By operating directly within the Linux kernel, Tetragon enables teams to monitor, detect, and enforce policies with unparalleled efficiency and precision.
This article explores how Tetragon leverages eBPF to deliver real-time insights into Kubernetes environments, enhance threat detection, and streamline policy enforcement. We’ll also look at how Coralogix amplifies these capabilities, offering powerful analytics, alerting, and visualization tools to turn Tetragon’s data into actionable intelligence for modern cloud-native ecosystems.
What is Tetragon?
Tetragon, developed by Cilium, is an open-source runtime security observability and enforcement platform. It leverages eBPF technology to provide real-time monitoring, detection, and enforcement of security policies directly within the Linux kernel. Tetragon enables fine-grained visibility into system activities without requiring intrusive instrumentation or modifying application code.
What is eBPF anyway…?
Extended Berkeley Packet Filter is a revolutionary technology in the Linux kernel that allows programs to run safely and efficiently within the kernel space without modifying kernel source code or adding modules.
eBPF provides a programmable interface to dynamically attach small programs to kernel-level events, such as system calls, network packets, and file operations, enabling deep observability and control over system behavior.
Unlike traditional observability solutions, eBPF operates at the kernel level, providing unparalleled visibility into application and system events with minimal overhead.
Traditional methods often rely on user-space instrumentation or kernel modules, which can be intrusive, require context switching, and may introduce performance penalties. In contrast, eBPF programs execute directly in the kernel’s execution context, offering high-performance data collection and real-time insights without the need for costly polling or extensive logging.
This unique capability makes eBPF an ideal foundation for modern observability, security, and performance monitoring tools.
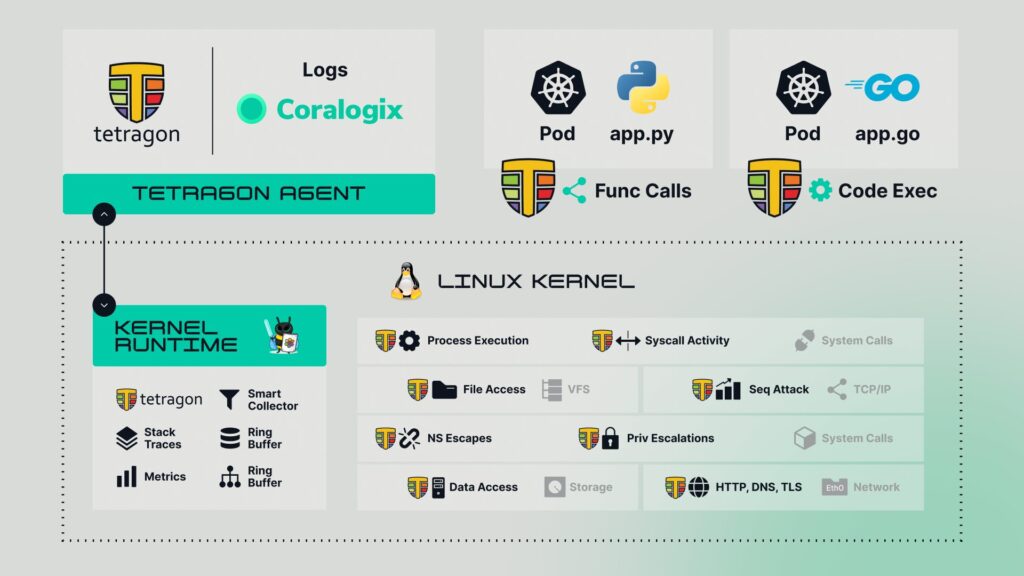
Application and Usage In Kubernetes
By combining eBPF’s kernel-level observability with Tetragon’s Kubernetes-native capabilities, teams can achieve a high-performance, secure, scalable observability and security solution tailored for modern cloud-native environments.
Real-Time Observability
Extends eBPF’s capabilities to provide real-time monitoring of process execution, file access, and network activity for Kubernetes pods and nodes.
Tracks workload behaviors at a granular level to aid in debugging, compliance, and performance optimization.
Runtime Threat Detection
Can detect anomalous behaviors and security threats within Kubernetes clusters, such as unauthorized process execution, suspicious file writes, or network connections.
Useful for identifying and responding to active threats without waiting for postmortem analysis.
Native Kubernetes Integration
Integrates with Kubernetes metadata (e.g., pods, namespaces, labels), mapping observability data to specific workloads and clusters, and provides a Kubernetes-aware view of security events, making it easier to manage and enforce security at the application level.
Policy Enforcement
Enforces granular security policies directly in the kernel, tailored to specific workloads or namespaces in the Kubernetes cluster.
Enhanced Forensics and Audit Capability
Captures detailed logs of system events, making it easier to perform root-cause analysis or audits for compliance requirements making it extremely useful for tracing back the origin of security incidents or debugging application issues.
Scalability for Large Clusters
Designed to operate efficiently at scale, leveraging eBPF’s low overhead to monitor large Kubernetes deployments without impacting performance making it suitable for environments with dynamic workloads where traditional tools struggle to keep up or are less scaleable.
Lightweight Agent Deployment
Tetragon agents run as lightweight daemons on Kubernetes nodes, avoiding the need for complex instrumentation or sidecar containers.
How it all comes together
Coralogix enhances the observability and operational insights of Tetragon by leveraging advanced log correlation, powerful alerting mechanisms, and intuitive visualizations. Coralogix allows users to unify Tetragon’s detailed runtime logs with data from other sources such as cloud platforms such as AWS, application logs, and network traffic.
This centralization enables users to correlate eBPF-driven insights, such as process execution or anomalous system calls, with other contextual information, like application behavior or network activity. Such correlations provide a holistic view of the cluster, making it easier to troubleshoot issues, detect threats, and optimize system performance.
The alerting capabilities enable real-time notifications based on predefined or custom thresholds, patterns, or anomalies in the logs. For example, users can configure alerts for specific eBPF-detected events like privilege escalations or unauthorized file access. These alerts are enriched with Kubernetes metadata (e.g., pod name, namespace) and provide actionable context for rapid incident response.
Customized dashboards are available to display actions and trends derived from Tetragon events, such as process activity, and system call distributions. By combining these insights with Kubernetes performance data, users gain a comprehensive view of their environment in an intuitive format. This facilitates proactive performance tuning, compliance auditing, and security posture evaluation.
In short, Coralogix amplifies Tetragon’s capabilities by turning its granular kernel-level observability into actionable intelligence, seamlessly integrated into the broader ecosystem of a Kubernetes monitoring strategy.
Learn more about Coralogix security here.
Book a demo
Complete this form to speak with one of our sales representatives.