Your defense playbook
-

- Security
MongoBleed (CVE-2025-14847): Critical Unauthenticated MongoDB Memory Disclosure
-

- Kubernetes
- Security
Building visibility and resilience across Kubernetes
-

- Security
Mastering Web Application Security: Enterprise-Grade OWASP Detection Rules for AWS WAF, Akamai, F5 and Cloudflare
-

- MDR
- Security
Threat Intel Update: November 2025
-

- Observability
- Security
Raising the Bar in Observability and Security: Coralogix Extensions at Scale
-

- Product
- Security
Coralogix Expands Unified Threat Intelligence Coverage
-

- Security
VPC Flow Logs – Everything you need to know
-

Mamona Ransomware (RAAS) – Offline Commodity Ransomware with Custom Encryption
-

- Security
Securing NHIs with Coralogix
-

- Security
Best Practices for Monitoring Database Activity
-

GitHub Action Supply Chain Attack (CVE-2025-30066)
-

- Security
Honey Tokens: Turning Attackers’ Curiosity into a Security Advantage Using Coralogix
-

- Observability
- Security
Eliminating Blind Spots: The Case for Integrated Security and Observability
-

How Meesho Strengthened it’s GCP Security Posture with Snowbit by Coralogix
-

- Security
Threat Hunting with AWS CloudTrail: Detecting Anomalies for a Secure Cloud Environment
-

Fortinet Firewall Authentication Bypass Vulnerability (CVE-2024-55591)
-

- Observability
- Security
How Tetragon Redefines Security and Observability
-

CoinDCX Centralizes Monitoring, Compliance, and Intelligence with Snowbit by Coralogix
-

- MDR
Offensive security assessment: detect, defend and deter
-
- Security
Using VPC Flow Logs to Monitor and Optimize Your Network Traffic
-

- Security
Amazon Route53: Best practices, security monitoring use cases
-

Unified Insights: Strengthening Security Through Observability
-

How to Choose the Right Security Monitoring Tool
-

- Security
- SIEM
SIEM Tutorial: What should a good SIEM Provider do for you?
-
- Security
Optimized Traffic Mirroring Examples – Part 2
-

- Security
Optimized Security Traffic Mirroring Examples – Part 1
-

- Security
Have You Forgotten About Application-Level Security?
-

- Security
5 Cybersecurity Tools to Safeguard Your Business
-

- Product
- Security
What’s the Most Powerful Tool in Your Security Arsenal?
-

- Security
What is Red Teaming in Cyber Security? The Complete Guide
-

- Security
What is a Security Whitelist?
-

- Product
- Security
How to Use SIEM Tools in the Modern World
-
- Observability
- Security
How do Observability and Security Work Together?
-
- Security
Threat Intelligence Feeds: A Complete Overview
-
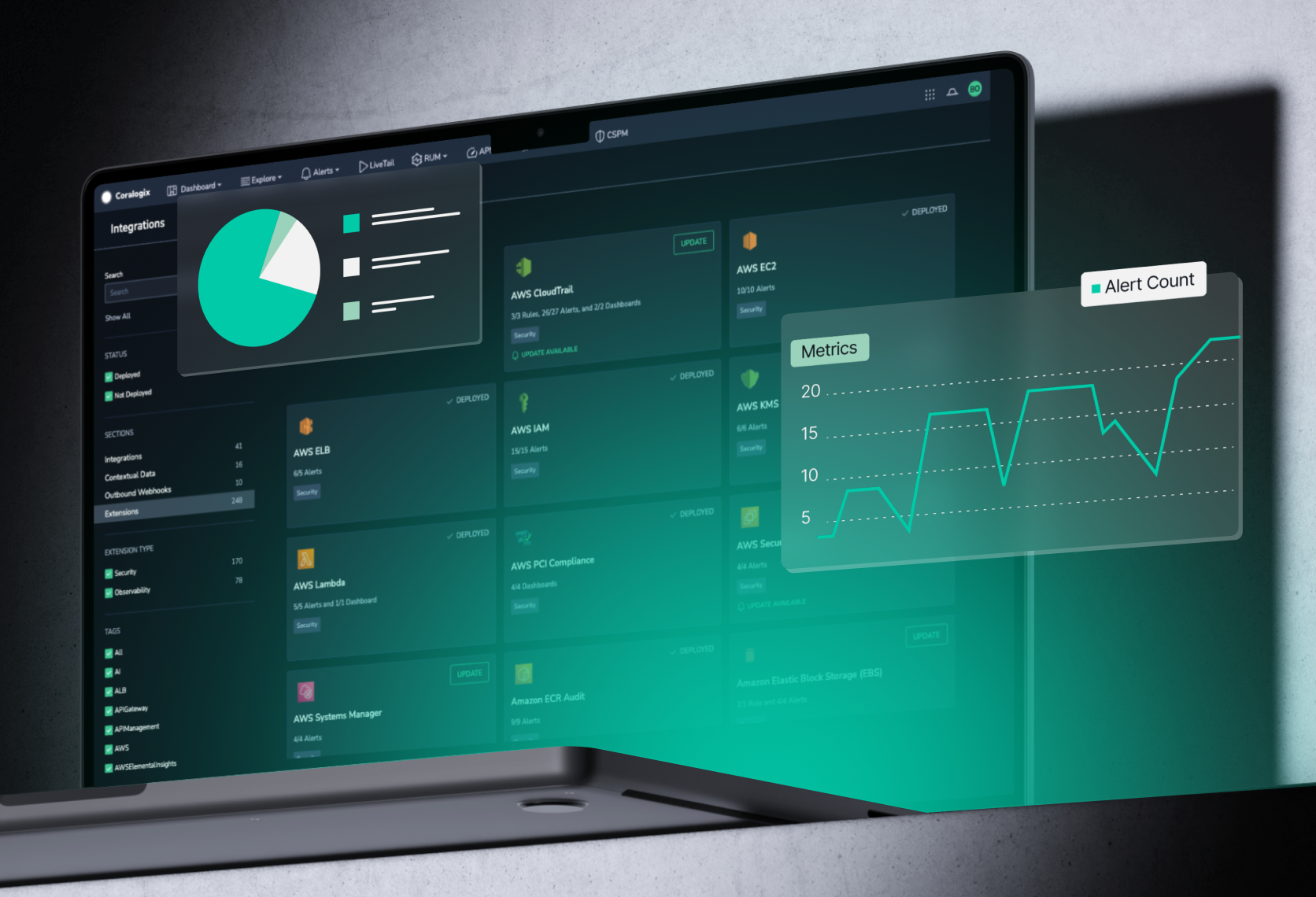
- Security
Security Insights: Over 1,000 Alerts & Dashboards in One Click
-

- MDR
- Security
Beating the Security Talent Problem: The SRC Solution
-
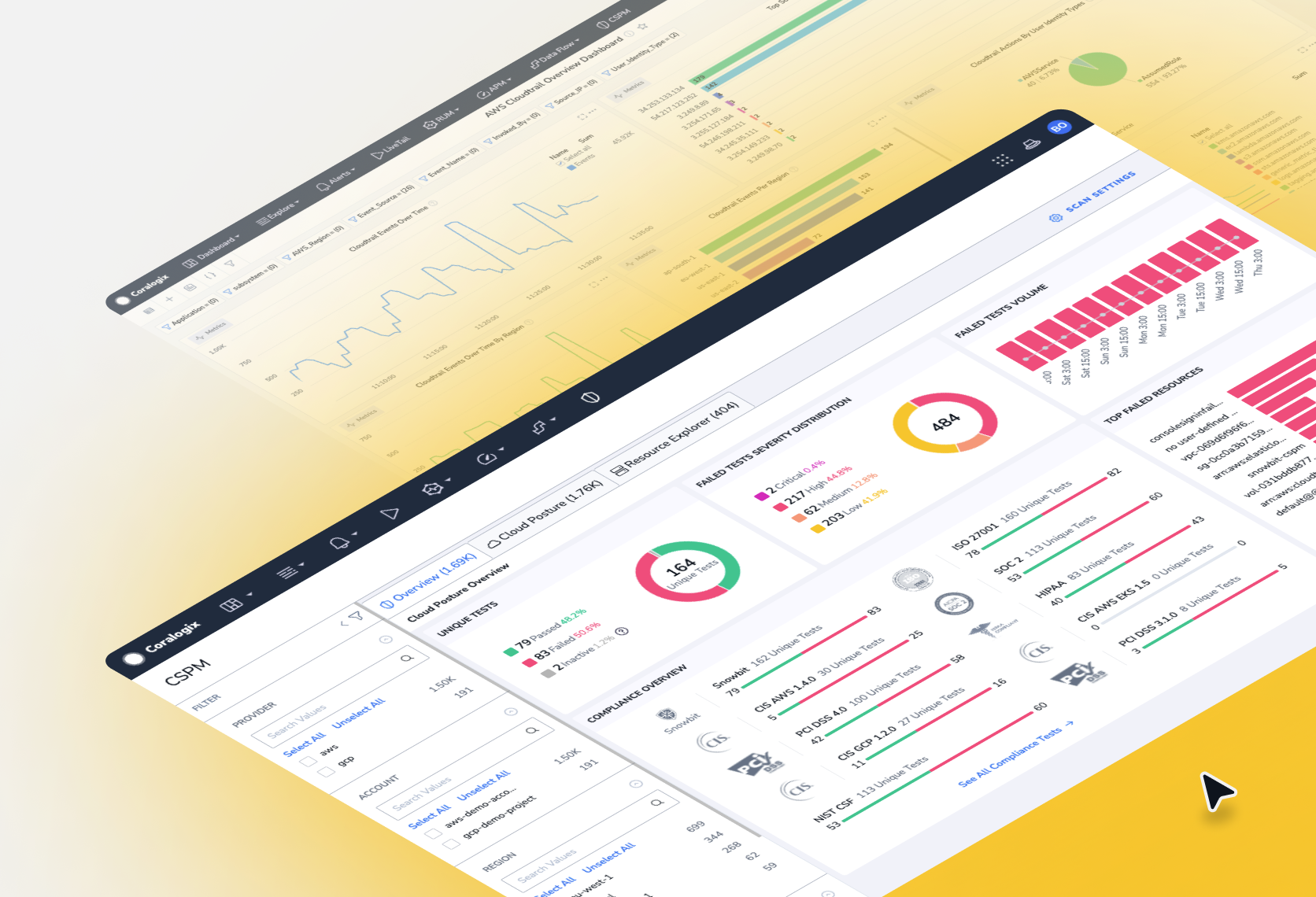
- Product
- Security
PCI DSS compliance with SIEM, CSPM and MDR
-

- Security
AWS IAM Best Practices
-
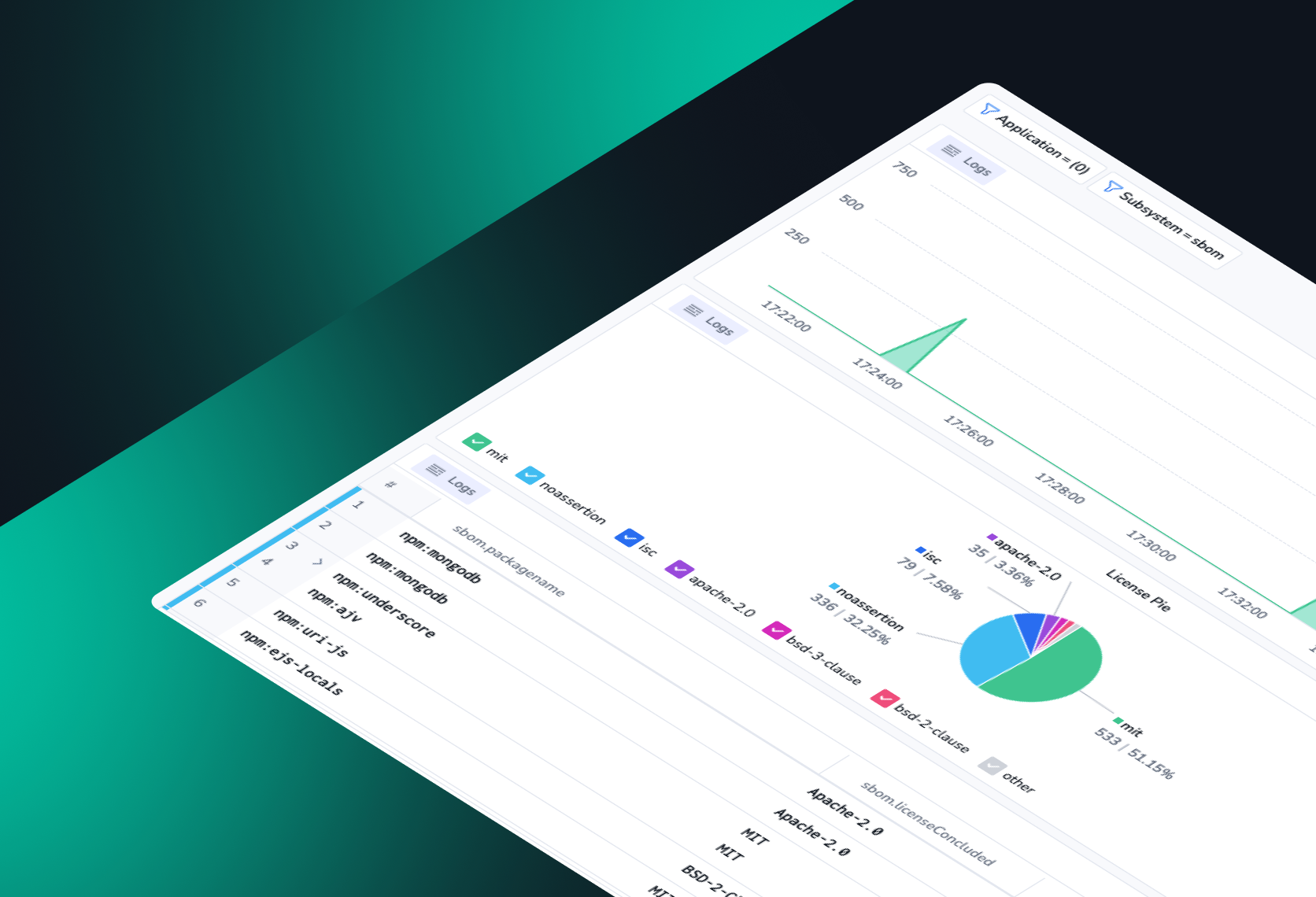
- Security
Track SBOM Compliance with Coralogix
-
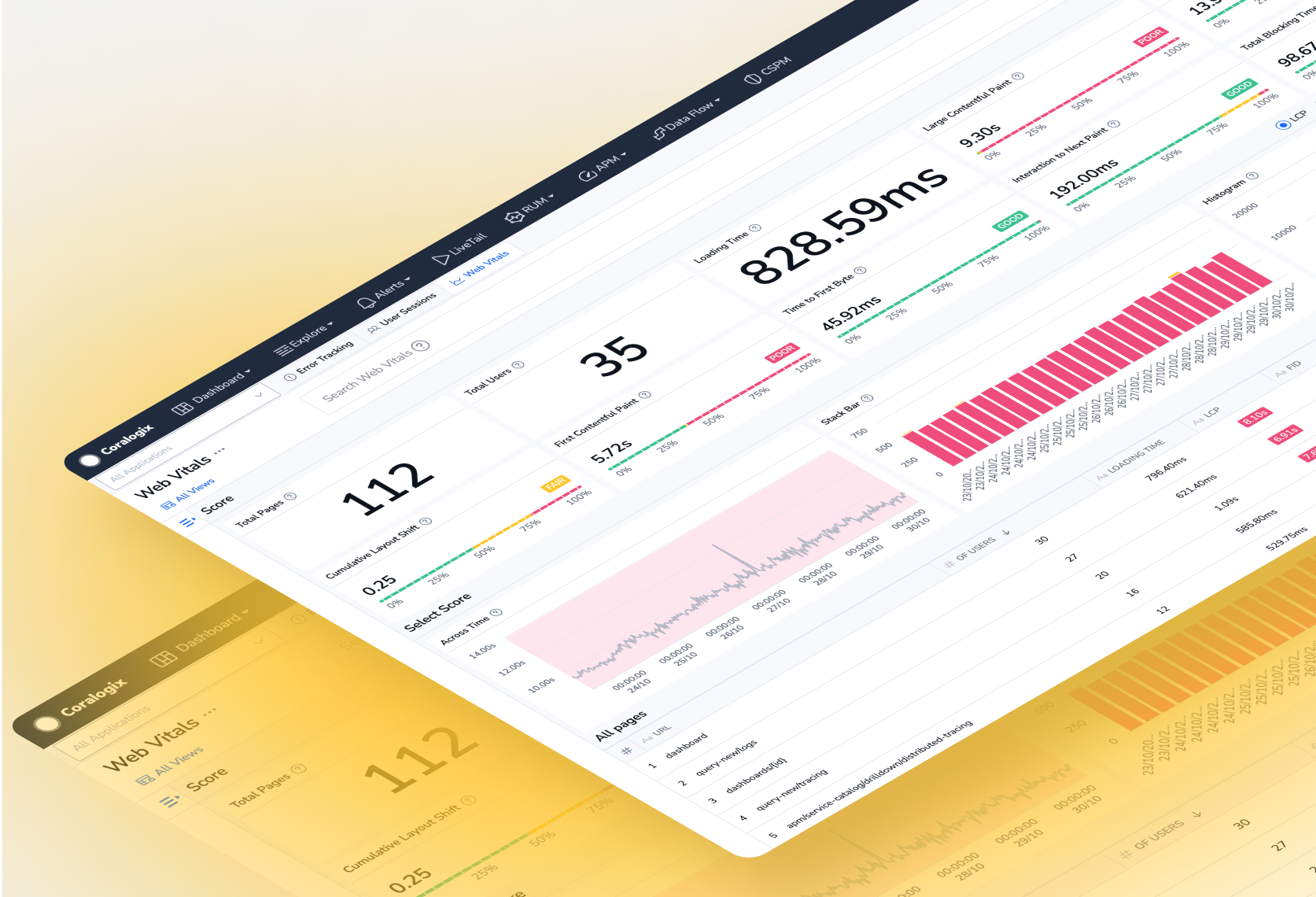
- Product
How Coralogix Investigations Speeds Up Root Cause Analysis
-
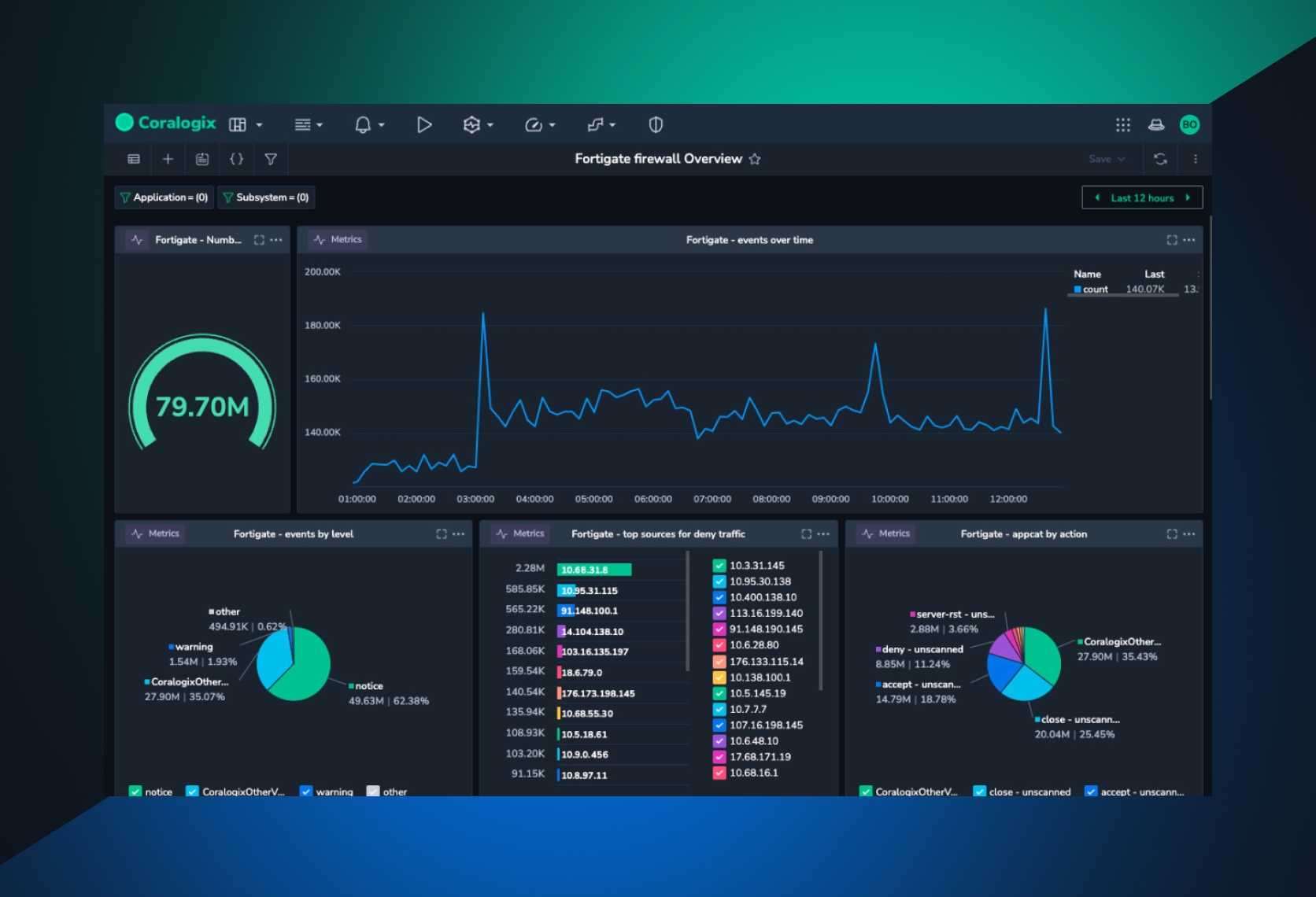
- Security
FortiGate Firewall – Top 10 Best Practices
-

- Observability
- Security
What is the Benefit of Including Security with Your Observability Strategy?
-

Building a Secure Workforce Management Platform: When I Work’s Implementation of Snowbit
-

Scaling Success: How MaestroQA Optimized AWS Observability & Security with Coralogix & Snowbit