

What’s included:
- IOC visibility→ Overview of newly added IOCs that are automatically integrated into your protection layer
- Threat actor insights → Details on top APT groups, ransomware operators, and campaigns we’ve tracked this month
- Exploitation trends → Insights into the most exploited CVEs and active vulnerabilities observed globally
- Actionable intelligence → All IOCs are enriched with context — including threat actors, TTPs, and relevance scoring
What this means for you:
- Enhanced visibility → Get a clear understanding of trending threats, campaigns, and global exploit activity
- Continuous protection → Your environment benefits automatically from up-to-date threat intelligence without manual intervention
- Strategic awareness → Stay informed about global threat activity without operational overhead
- No additional action required → All newly added IOCs are already integrated into our detection and alerting mechanisms
Threat insights
Major cloud attack vectors
- AWS infrastructure targeting: Crimson Collective actively harvesting exposed AWS credentials, creating IAM users with AdministratorAccess, resetting RDS passwords, and snapshotting EBS volumes for data exfiltration
- Azure entra ID exploitation: Critical privilege escalation vulnerability (CVE-2025-59246) enabling unauthorized access to cloud identity infrastructure
- F5 BIG-IP nation-state breach: 266,000+ instances exposed online following long-term compromise of product development environments by Chinese APT ( UNC 5291 )
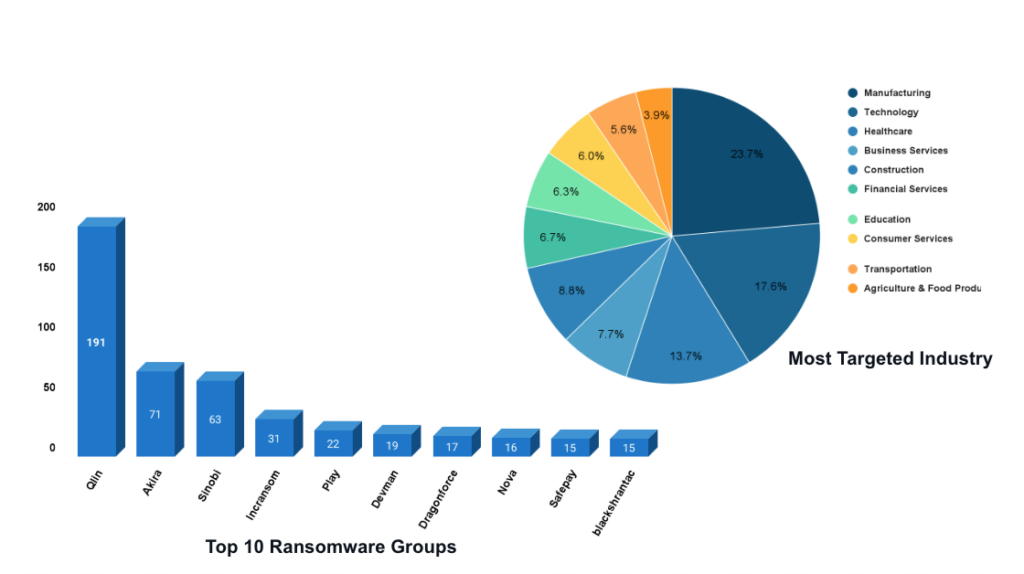
Ransomware activity
- Top groups: Qilin, Akira, and Snobi were the most active ransomware groups during this period
- Key exploits: CVE-2025-61882 (Oracle E-Business Suite) actively weaponized by Cl0p for initial access and data theft
- Evolution: Multi-platform capabilities with ESXi/vSphere targeting, enhanced anti-analysis, faster encryption algorithms
Critical CVEs
- Top actively exploited CVEs impacting cloud infrastructure, including Oracle EBS, Azure Entra ID, F5 BIG-IP, VMware Aria Operations
- Zero-days patched: 3 Windows zero-days in October Patch Tuesday (CVE-2025-59230, CVE-2025-24990, CVE-2025-47827)
- Cloud-critical vulnerabilities: ASP.NET Core Kestrel, Redis, Adobe Commerce (Magento), Linux sudo under active exploitation
Key trends in supply chain, cloud, & AI
Supply chain: Third-party integration compromise High-profile breaches at Qantas and MANGO demonstrated a shift to targeting third-party platforms integrated with core business systems like Salesforce. Attackers compromised marketing vendors and integrated apps to gain trusted access to customer data, bypassing traditional perimeter defenses.
Supply chain: “Living-off-the-Trusted-Stack” (LOTTS) Chinese-linked actors were observed weaponizing the legitimate, open-source Nezha monitoring tool. By abusing this trusted software, they successfully delivered the Gh0st RAT malware, inheriting privileged access and remaining undetected by traditional endpoint security solutions.
Cloud abuse: AWS-native attack playbook The Crimson Collective group executed a full-lifecycle attack on AWS environments. After compromising exposed IAM credentials, they escalated privileges to ‘AdministratorAccess’ and used the victim’s own AWS Simple Email Service (SES) to send extortion notes, guaranteeing deliverability and amplifying pressure.
AI abuse (offensive): AI-generated malware in the wild The state-aligned actor UTA0388 was confirmed to be using OpenAI’s ChatGPT as a force multiplier. The group used the public AI to develop a custom malware family (GOVERSHELL) and to craft highly convincing, context-aware phishing emails at scale.
AI abuse (internal): “Shadow AI” data exposure A global analysis revealed that 1 in 54 employee prompts into public GenAI tools contains high-risk sensitive data. This “Shadow AI” phenomenon has become a massive, unmonitored data loss vector, with 91% of organizations found to be regularly leaking proprietary information.
Most exploited- CVE
CVE-2025-61882 — Oracle E-Business Suite BI Publisher (10.0)
- Description: Unauthenticated remote code execution via the BI Publisher Integration component with a single low-complexity HTTP request, allowing data theft from internet-exposed EBS applications.
- EPSS: High Published: October 2025 CISA KEV Added: October 2025 Actively Exploited: Yes
CVE-2025-59287 — Microsoft Windows Server Update Service (9.8)
- Description: Remote code execution vulnerability via deserialization in Windows Server Update Service. Microsoft released out-of-band emergency update on October 23 to better address this critical flaw beyond the October Patch Tuesday fix.
- EPSS: High Published: 2025-10-08 CISA KEV Added: 2025-10-08 Actively Exploited: Likely
CVE-2025-10035 — Fortra GoAnywhere MFT (10.0)
- Description: Unauthorized third-party access to file transfer systems, primarily affecting systems with internet-exposed admin console. The flaw enables significant data theft and has been exploited since at least September 10, 2025.
- EPSS: 81.06% Published: September 2025 CISA KEV Added: September 2025 Actively Exploited: Yes
CVE-2025-49844 — Redis Lua Engine (Critical)
- Description: Use-after-free RCE in the default-enabled Lua engine affecting all Redis versions. Authenticated exploits enable sandbox escape and full host compromise (reverse shells, credential theft, lateral movement, malware).
- EPSS: High Published: October 2025 CISA KEV Added: October 2025 Actively Exploited: Yes (botnets and ransomware)
Indicators covered
Over the past month, we have expanded our threat intelligence coverage by integrating new Indicators of Compromise (IOCs) associated with the following ransomware groups,malwares and threat actors:
Ransomware & threat actor groups:
- Clop Ransomware
- Qilin Ransomware
- Conti Ransomware
- Anylock Ransomware
- Babuk Ransomware
- Yurei Ransomware
- Radar Ransomware
- Crimson Collective
- Lazarus Group
- Storm-2603
Malware & botnets
- Govershell
- Vampire Bot
- ClayRat
- Ghost Rat
- Amadey Stealer
- Lumma Stealer
- Redline Stealer
- RondoDox Botnet
- Clearfake
- ClickFix
- Amos Stealer
- XWorm RAT
- Katz Stealer
- Retro C2
And many more ….
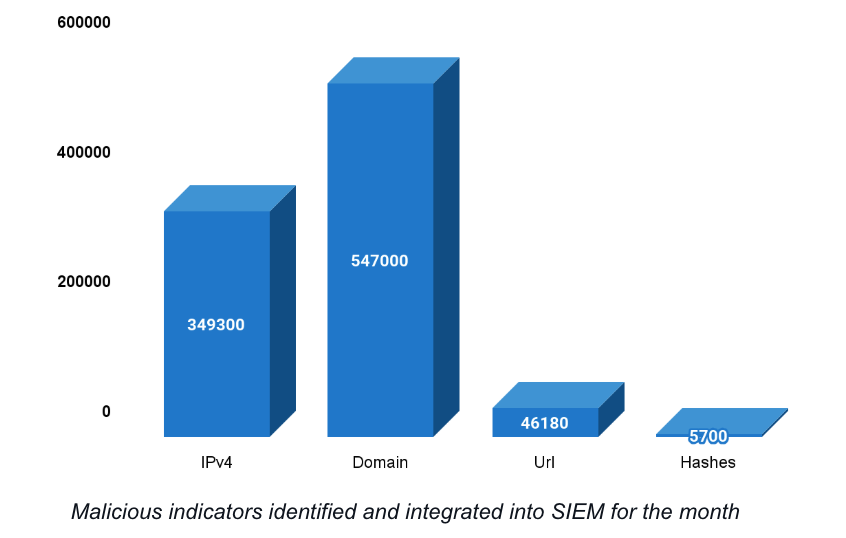
Monthly IOC added
Ransomware activity
Book a demo
Complete this form to speak with one of our sales representatives.
